- Simple architecture and modern encryption: per-peer keys and AllowedIPs for routing.
- Quick installation on Linux and official apps for desktop and mobile.
- Superior performance to IPsec/OpenVPN, with roaming and low latency.

If you're looking for a VPN that is fast, secure and easy to deploy, WireGuard It's the best you can use today. With a minimalist design and modern cryptography, it's ideal for home users, professionals, and corporate environments, both on computers and on mobile devices and routers.
In this practical guide you will find everything from the basics to the advanced settings: Installation on Linux (Ubuntu/Debian/CentOS), keys, server and client files, IP forwarding, NAT/Firewall, applications on Windows/macOS/Android/iOS, split tunneling, performance, troubleshooting, and compatibility with platforms such as OPNsense, pfSense, QNAP, Mikrotik or Teltonika.
What is WireGuard and why choose it?
WireGuard is an open source VPN protocol and software designed to create L3 encrypted tunnels over UDP. It stands out compared to OpenVPN or IPsec due to its simplicity, performance and lower latency, relying on modern algorithms such as Curve25519, ChaCha20-Poly1305, BLAKE2, SipHash24 and HKDF.
Its code base is very small (around thousands of lines), which facilitates audits, reduces attack surface and improves maintenance. It is also integrated into the Linux kernel, allowing high transfer rates and agile response even on modest hardware.
It is multiplatform: there are official apps for Windows, macOS, Linux, Android and iOS, and support for router/firewall-oriented systems like OPNsense. It's also available for environments like FreeBSD, OpenBSD, and NAS and virtualization platforms.
How it works inside
WireGuard establishes an encrypted tunnel between peers (peers) identified by keys. Each device generates a key pair (private/public) and shares only its public key with the other end; from there, all traffic is encrypted and authenticated.
The directive AllowedIPs Defines both the outgoing routing (what traffic should go through the tunnel) and the list of valid sources that the remote peer will accept after successfully decrypting a packet. This approach is known as Cryptokey Routing and greatly simplifies traffic policy.
WireGuard is excellent with the roaming- If your client's IP changes (e.g., you jump from Wi-Fi to 4G/5G), the session is reestablished transparently and very quickly. It also supports kill switch to block traffic out of the tunnel if the VPN goes down.
Installation on Linux: Ubuntu/Debian/CentOS
On Ubuntu, WireGuard is available in the official repos. Update the packages and then install the software to get the module and tools. wg and wg-quick.
apt update && apt upgrade -y
apt install wireguard -y
modprobe wireguardIn Debian stable you can rely on unstable branch repos if you need to, following the recommended method and with care in production:
sudo sh -c 'echo deb https://deb.debian.org/debian/ unstable main > /etc/apt/sources.list.d/unstable.list'
sudo sh -c 'printf "Package: *\nPin: release a=unstable\nPin-Priority: 90\n" > /etc/apt/preferences.d/limit-unstable'
sudo apt update
sudo apt install wireguardIn CentOS 8.3 the flow is similar: you activate EPEL/ElRepo repos if necessary and then install the package WireGuard and corresponding modules.
Key generation
Each peer must have its own private/public key pair. Apply umask to restrict permissions and generate keys for the server and clients.
umask 077
wg genkey | tee privatekey | wg pubkey > publickeyRepeat on each device. Never share the private key and save both safely. If you prefer, create files with different names, for example privatekeyserver y publicserverkey.
Server configuration
Create the main file in /etc/wireguard/wg0.conf. Assign a VPN subnet (not used on your real LAN), the UDP port and add a block [Peer] per authorized customer.
[Interface]
Address = 10.0.0.1/24
ListenPort = 51820
PrivateKey = <clave_privada_servidor>
# Cliente 1
[Peer]
PublicKey = <clave_publica_cliente1>
AllowedIPs = 10.0.0.2/32You can also use another subnet, for example 192.168.2.0/24, and grow with multiple peers. For rapid deployments, it is common to use wg-quick with wgN.conf files.
Client configuration
On the client create a file, for example wg0-client.conf, with its private key, tunnel address, optional DNS, and the server's peer with its public endpoint and port.
[Interface]
PrivateKey = <clave_privada_cliente>
Address = 10.0.0.2/24
DNS = 8.8.8.8
[Peer]
PublicKey = <clave_publica_servidor>
Endpoint = <ip_publica_servidor>:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25If you put AllowedIPs = 0.0.0.0/0 All traffic will go through the VPN; if you only want to reach specific server networks, limit it to the necessary subnets and you will reduce latency and consumption.
IP Forwarding and NAT on the Server
Enable forwarding so clients can access the Internet through the server. Apply changes on the fly with sysctl.
echo 'net.ipv4.ip_forward=1' >> /etc/sysctl.conf
echo 'net.ipv6.conf.all.forwarding=1' >> /etc/sysctl.conf
sysctl -pConfigure NAT with iptables for the VPN subnet, setting the WAN interface (for example, eth0):
iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADEMake it persistent with the appropriate packages and save rules to be applied on system reboot.
apt install -y iptables-persistent netfilter-persistent
netfilter-persistent saveStartup and verification
Bring up the interface and enable the service to start with the system. This step creates the virtual interface and adds routes necessary.
systemctl start wg-quick@wg0
systemctl enable wg-quick@wg0
wgWith wg You'll see the peers, keys, transfers, and last handshake times. If your firewall policy is restrictive, allow entry through the interface. wg0 and the UDP port of the service:
iptables -I INPUT 1 -i wg0 -j ACCEPT
Official apps: Windows, macOS, Android, and iOS
On the desktop you can import a .conf file. On mobile devices, the app allows you to create the interface from a QR code containing the configuration; it is very convenient for non-technical customers.
If your goal is to expose self-hosted services such as Plex/Radarr/Sonarr Through your VPN, simply assign IPs in the WireGuard subnet and adjust AllowedIPs so the client can reach that network; you don't need to open additional ports to the outside if all access is through the tunnel.
Advantages and disadvantages
WireGuard is very fast and simple, but it's important to consider its limitations and specificities depending on the use case. Here's a balanced overview of the most relevant.
| Advantages | Disadvantages |
|---|---|
| Clear and short configuration, ideal for automation | Does not incorporate native traffic obfuscation |
| High performance and low latency even in mobiles | In some legacy environments there are fewer advanced options |
| Modern cryptography and small code that makes it easy audit | Privacy: IP/public key association may be sensitive depending on policies |
| Seamless roaming and kill switch available on clients | Third-party compatibility is not always homogeneous |
Split tunneling: directing only what is necessary
Split tunneling allows you to send only the traffic you need through the VPN. With AllowedIPs You decide whether to do full or selective redirection to one or more subnets.
# Redirección completa de Internet
[Peer]
AllowedIPs = 0.0.0.0/0# Solo acceder a recursos de la LAN 192.168.1.0/24 por la VPN
[Peer]
AllowedIPs = 192.168.1.0/24There are variants such as reverse split tunneling, filtered by URL or by application (through specific extensions/clients), although the native basis in WireGuard is control by IP and prefixes.
Compatibility and ecosystem
WireGuard was born for the Linux kernel, but today it is multiplatformOPNsense integrates it natively; pfSense was temporarily discontinued for audits, and it was subsequently offered as an optional package depending on the version.
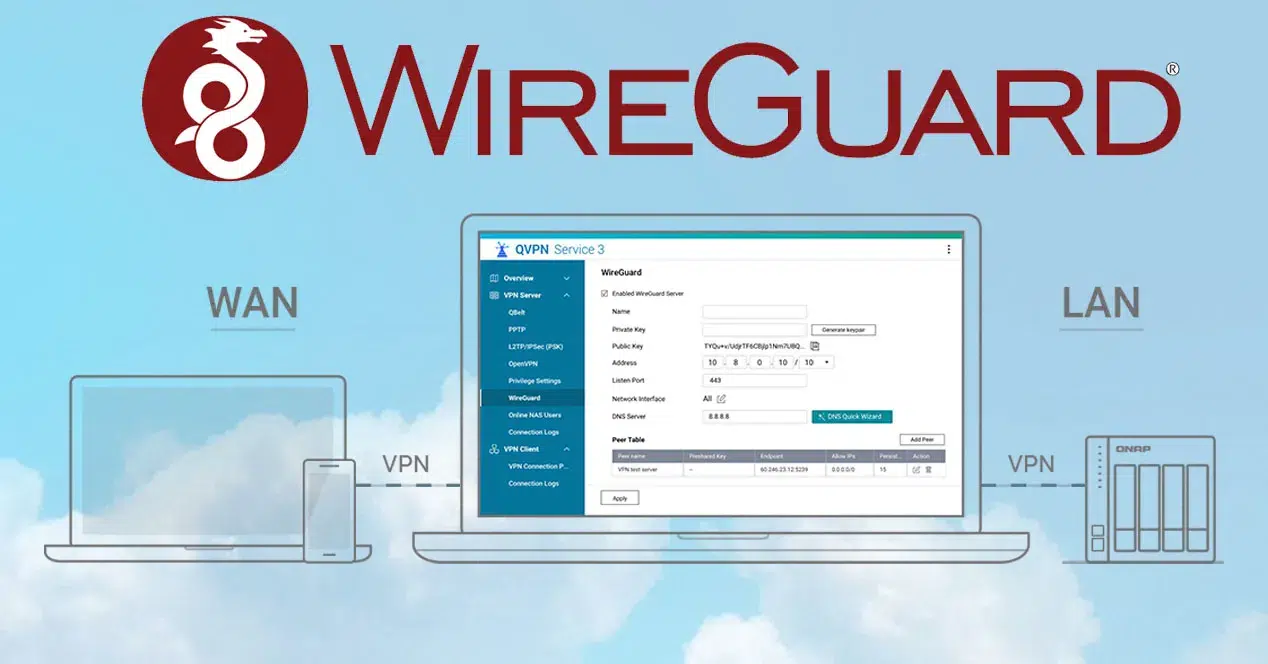
On NAS like QNAP you can mount it via QVPN or virtual machines, taking advantage of 10GbE NICs to high speedsMikroTik router boards have incorporated WireGuard support since RouterOS 7.x; in its early iterations, it was in beta and not recommended for production, but it does allow P2P tunnels between devices and even end clients.
Manufacturers like Teltonika have a package to add WireGuard to their routers; if you need equipment, you can purchase them at shop.davantel.com and follow the manufacturer's guidelines for installation packages extra.
Performance and latency
Thanks to its minimalist design and the choice of efficient algorithms, WireGuard achieves very high speeds and low latencies, generally superior to L2TP/IPsec and OpenVPN. In local tests with powerful hardware, the actual rate is often double that of the alternatives, making it ideal for streaming, gaming or VoIP.
Corporate implementation and teleworking
In the enterprise, WireGuard is suitable for creating tunnels between offices, remote employee access, and secure connections between CPD and cloud (e.g., for backups). Its concise syntax makes versioning and automation easy.
It integrates with directories such as LDAP/AD using intermediate solutions and can coexist with IDS/IPS or NAC platforms. A popular option is PacketFence (open source), which allows you to verify the status of equipment before granting access and control BYOD.
Windows/macOS: Notes and Tips
The official Windows app usually works without problems, but in some versions of Windows 10 there have been issues when using AllowedIPs = 0.0.0.0/0 due to route conflicts. As a temporary alternative, some users opt for WireGuard-based clients like TunSafe or limiting AllowedIPs to specific subnets.
Debian Quick Start Guide with Example Keys
Generate keys for server and client in /etc/wireguard/ and create the wg0 interface. Make sure the VPN IPs don't match any other IPs on your local network or your clients.
cd /etc/wireguard/
wg genkey | tee claveprivadaservidor | wg pubkey > clavepublicaservidor
wg genkey | tee claveprivadacliente1 | wg pubkey > clavepublicacliente1wg0.conf server with subnet 192.168.2.0/24 and port 51820. Enable PostUp/PostDown if you want to automate NAT with iptables when bringing up/bringing down the interface.
[Interface]
Address = 192.168.2.1/24
PrivateKey = <clave_privada_servidor>
ListenPort = 51820
#PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
#PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = <clave_publica_cliente1>
AllowedIPs = 0.0.0.0/0Client with address 192.168.2.2, pointing to the server's public endpoint and with keepalive optional if there is intermediate NAT.
[Interface]
PrivateKey = <clave_privada_cliente1>
Address = 192.168.2.2/32
[Peer]
PublicKey = <clave_publica_servidor>
AllowedIPs = 0.0.0.0/0
Endpoint = <ip_publica_servidor>:51820
#PersistentKeepalive = 25Pull up the interface and watch as the MTU, route markings, and fwmark and routing policy rules. Review the wg‑quick output and status with wg show.
Mikrotik: tunnel between RouterOS 7.x
MikroTik has supported WireGuard since RouterOS 7.x. Create a WireGuard interface on each router, apply it, and it will be generated automatically. keys. Assign IPs to Ether2 as WAN and wireguard1 as tunnel interface.
Configure the peers by crossing the server's public key on the client side and vice versa, define Allowed Address/AllowedIPs (for example 0.0.0.0/0 if you want to allow any source/destination through the tunnel) and set the remote endpoint with its port. A ping to the remote tunnel IP will confirm the handshake.
If you connect mobile phones or computers to the Mikrotik tunnel, fine-tune the allowed networks so as not to open more than necessary; WireGuard decides the flow of packets based on your Cryptokey Routing, so it is important to match origins and destinations.
Cryptography used
WireGuard employs a modern set of: Noise as a framework, Curve25519 for ECDH, ChaCha20 for authenticated symmetric encryption with Poly1305, BLAKE2 for hashing, SipHash24 for hash tables and HKDF for derivation of keysIf an algorithm is deprecated, the protocol can be versioned to migrate seamlessly.
Pros and cons on mobile
Using it on smartphones allows you to browse safely on Public Wi-Fi, hide traffic from your ISP, and connect to your home network to access NAS, home automation, or gaming. On iOS/Android, switching networks doesn't take down the tunnel, which improves the experience.
As cons, you drag some loss of speed and greater latency compared to direct output, and you depend on the server always being available. However, compared to IPsec/OpenVPN the penalty is usually lower.
WireGuard combines simplicity, speed, and real security with a gentle learning curve: install it, generate keys, define AllowedIPs, and you're ready to go. Add IP forwarding, well-implemented NAT, official apps with QR codes, and compatibility with ecosystems like OPNsense, Mikrotik, or Teltonika. a modern VPN for almost any scenario, from securing public networks to connecting headquarters and accessing your home services without headaches.
Editor specialized in technology and internet issues with more than ten years of experience in different digital media. I have worked as an editor and content creator for e-commerce, communication, online marketing and advertising companies. I have also written on economics, finance and other sectors websites. My work is also my passion. Now, through my articles in Tecnobits, I try to explore all the news and new opportunities that the world of technology offers us every day to improve our lives.