- Process Hacker is an advanced, open-source, and free process manager that offers much deeper control than the standard Task Manager.
- It allows you to manage processes, services, network, disk and memory in detail, including advanced functions such as forced closure, priority changes, handle search and memory dumps.
- Its kernel-mode driver enhances the termination of protected processes, although in 64-bit Windows it is limited by driver signing policies.
- It is a key tool for diagnosing performance problems, debugging applications, and supporting security investigations, provided it is used with caution.

For many Windows users, Task Manager falls short. That's why some end up turning to Process Hacker. This tool has gained popularity among administrators, developers, and security analysts because it allows them to view and control the system at a level that the standard Windows Task Manager can't even imagine.
In this comprehensive guide we will review What is Process Hacker, how to download and install itWhat it offers compared to Task Manager and Process Explorer, and how to use it to manage processes, services, network, disk, memory, and even investigate malware.
What is Process Hacker and why is it so powerful?
Process Hacker is, basically, an advanced process manager for WindowsIt's open source and completely free. Many people describe it as "Task Manager on steroids," and the truth is, that description fits it quite well.
Its goal is to give you a a very detailed view of what is happening in your systemProcesses, services, memory, network, disk… and, above all, giving you tools to intervene when something gets stuck, consumes too many resources, or seems suspicious of malware. The interface is somewhat reminiscent of Process Explorer, but Process Hacker adds a good number of extra features.
One of its strengths is that it can detect hidden processes and terminate “shielded” processes which the Task Manager cannot close. This is achieved thanks to a kernel-mode driver called KProcessHacker, which allows it to communicate directly with the Windows kernel with elevated privileges.
Being a project Open source, the code is available to anyoneThis fosters transparency: the community can audit it, detect security flaws, propose improvements, and ensure there are no hidden unpleasant surprises. Many companies and cybersecurity professionals trust Process Hacker precisely because of this open philosophy.
It is worth noting, however, that Some antivirus programs flag it as "risky" or a PUP (Potentially Unwanted Program).Not because it's malicious, but because it has the capacity to kill highly sensitive processes (including security services). It's a very powerful weapon and, like all weapons, it should be used judiciously.
Download Process Hacker: versions, portable version and source code
To get the program, the usual thing to do is go to their official oa page your repository on SourceForge / GitHubThere you will always find the latest version and a quick summary of what the tool can do.
In the downloads section you will normally see two main modalities for 64-bit systems:
- Setup (Recommended): the classic installer, the one we've always used, recommended for most users.
- Binaries (portable): portable version, which you can run directly without installing.
The Setup option is ideal if you want Leave Process Hacker already installed.integrated with the Start menu and with additional options (such as replacing the Task Manager). The portable version, on the other hand, is perfect for carry it on a USB drive and use it on different computers without needing to install anything.
A little further down they also usually appear 32-bit versionsIn case you're still working with older equipment. They're not as common these days, but there are still environments where they're necessary.
If what interests you is tinkering with the source code Or you can compile your own build; on the official website you'll find a direct link to the GitHub repository. From there you can review the code, follow the changelog, and even suggest improvements if you'd like to contribute to the project.
The program weighs very little, around a few megabytesSo the download only takes a few seconds, even with a slow connection. Once it's finished, you can run the installer or, if you chose the portable version, extract and launch the executable directly.
Step-by-step installation on Windows
If you choose the installer (Setup), the process is fairly typical in Windows, although with Some interesting options worth checking out calmly.
As soon as you double-click on the downloaded file, Windows will display the User Account Control (UAC) It will warn you that the program wants to make changes to the system. This is normal: Process Hacker needs certain privileges to work its magic, so you'll have to accept to continue.
The first thing you'll see is the installation wizard with the typical license screenProcess Hacker is distributed under the GNU GPL version 3 license, with some specific exceptions mentioned in the text. It's a good idea to skim these before continuing, especially if you plan to use it in corporate environments.
In the next step, the installer suggests a default folder where the program will be copied. If the default path doesn't suit you, you can change it directly by typing another one, or by using the button Browse to select a different folder in the browser.
Then the component list that make up the application: main files, shortcuts, driver-related options, etc. If you want a complete installation, the simplest thing is to leave everything checked. If you know for sure you won't use a particular feature, you can deselect it, although the space it occupies is minimal.
Next, the assistant will ask you for the folder name in the Start menuIt usually suggests “Process Hacker 2” or something similar, which will create a new folder with that name. If you prefer the shortcut to appear in another existing folder, you can click Browse and choose it. You also have the option Don't create a Start Menu folder so that no entry is created in the Start menu.
On the next screen you will reach a set of additional options that do deserve special attention:
- To create or not a shortcut on desktopand decide whether it will be only for your user or for all users on the team.
- Start up Process Hacker at Windows startupAnd if in that case you want it to open minimized in the notification area.
- Make it Process Hacker replaces Task Manager Windows standard.
- Install the KProcessHacker driver and give it full access to the system (a very powerful option, but not recommended if you don't know what it entails).
Once you have chosen these preferences, the installer will show you a configuration summary And when you click Install, it will begin copying files. You'll see a small progress bar for a few seconds; the process is quick.
When finished, the assistant will notify you that the Installation has been completed successfully and will display several boxes:
- Run Process Hacker when closing the wizard.
- Open the changelog for the installed version.
- Visit the project's official website.
By default, only the box is usually checked. Run Process HackerIf you leave that option as is, when you click Finish the program will open for the first time and you can start experimenting with it.
How to start Process Hacker and first steps
If you chose to create a desktop shortcut during installation, launching the program will be as simple as double-click on the iconIt's the fastest way for those who use it often.
If you don't have direct access, you can always Open it from the Start menuSimply click the Start button, go to "All apps," and find the "Process Hacker 2" folder (or whatever name you chose during installation). Inside, you'll find the program entry and can open it with a click.
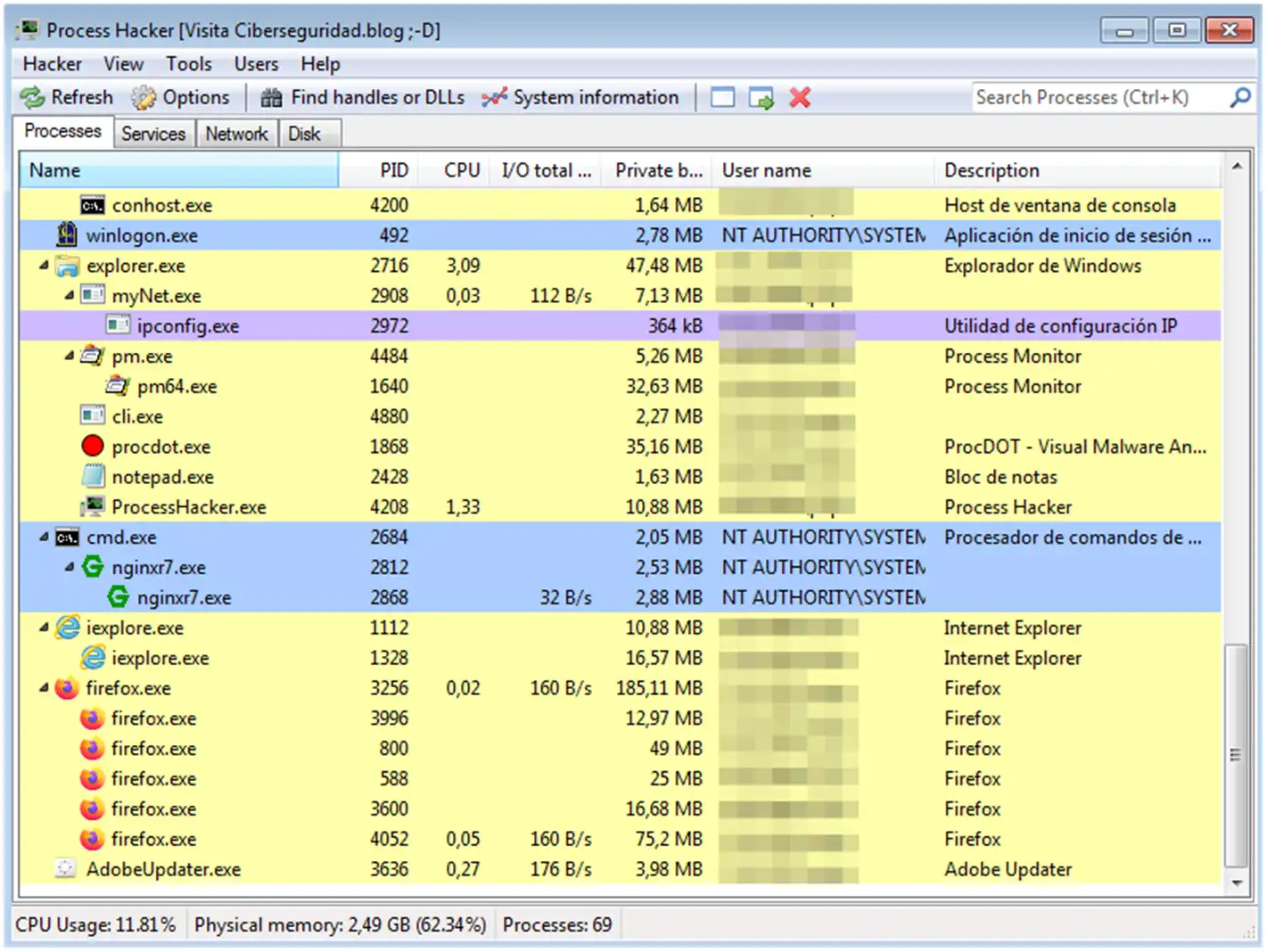
The first time it starts, what stands out is that the The interface is very information overloaded.Don't be alarmed: with a little practice, the layout becomes quite logical and organized. In fact, it displays much more data than the standard Task Manager, while still remaining manageable.
At the top you have a row of Main tabs: Processes, Services, Network, and DiskEach one shows you a different aspect of the system: running processes, services and drivers, network connections, and disk activity, respectively.
In the Processes tab, which is the one that opens by default, you will see all the processes in the form of a hierarchical treeThis means you can quickly identify which processes are parents and which are children. For example, it's common to see Notepad (notepad.exe) dependent on explorer.exe, as are many windows and applications you launch from the Explorer.
Processes tab: process inspection and control
The process view is the heart of Process Hacker. From here you can see what's actually running on your machine and make quick decisions when something goes wrong.
In the process list, in addition to the name, columns such as the PID (process identifier), percentage of CPU used, total I/O rate, memory in use (private bytes), user running the process and a brief description.
If you move the mouse and hold it for a moment over the name of a process, a window will open. pop-up box with additional detailsThe full path to the executable on disk (for example, C:\Windows\System32\notepad.exe), the exact file version, and the company that signed it (Microsoft Corporation, etc.). This information is very useful for distinguishing legitimate processes from potentially malicious imitations.
A curious aspect is that The processes are colored according to their type or state (services, system processes, suspended processes, etc.). The meaning of each color can be viewed and customized in the menu. Hacker > Options > Highlighting, in case you want to adapt the scheme to your liking.
If you right-click on any process, a menu will appear context menu full of optionsOne of the most striking is Properties, which appears highlighted and serves to open a window with extremely detailed information about the process.
That properties window is organized into multiple tabs (around eleven)Each tab focuses on a specific aspect. The General tab shows the executable path, the command line used to launch it, the running time, the parent process, the process environment block (PEB) address, and other low-level data.
The Statistics tab displays advanced statistics: process priority, number of CPU cycles consumed, amount of memory used by both the program itself and the data it handles, input/output operations performed (reads and writes to disk or other devices), etc.
The Performance tab offers CPU, memory, and I/O usage graphs For that process, something very useful for detecting spikes or anomalous behavior. Meanwhile, the Memory tab allows you to inspect and even directly edit the contents of the memory of the process, a very advanced functionality that is usually used in debugging or malware analysis.
In addition to Properties, the context menu includes a number of key options at the top:
- Terminate: ends the process immediately.
- Terminate Tree: closes the selected process and all its child processes.
- Suspend: temporarily freezes the process, which can be resumed later.
- Restart: restarts a process that has been suspended.
Using these options requires caution, because Process Hacker can terminate processes that other managers cannot.If you kill something critical to the system or an important application, you could lose data or cause instability. It's an ideal tool for stopping malware or unresponsive processes, but you need to know what you're doing.
Further down in the same menu, you will find settings for CPU priority In the Priority option, you can set levels ranging from Real time (maximum priority, the process gets the processor whenever it requests it) to Idle (minimum priority, it only runs if nothing else wants to use the CPU).
You also have the option I/O PriorityThis setting defines the process priority for input/output operations (reading and writing to disk, etc.) with values such as High, Normal, Low, and Very Low. Adjusting these options allows you, for example, to limit the impact of a large copy or a program that saturates the disk.
Another very interesting feature is Send toFrom there you can send information about the process (or a sample) to various online antivirus analysis services, which is great when you suspect a process might be malicious and want a second opinion without having to do all the work manually.
Service, network, and disk management
Process Hacker doesn't just focus on processes. The other main tabs give you a fairly fine control over services, network connections, and disk activity.
On the Services tab you will see a complete list of Windows services and driversThis includes both active and stopped services. From here, you can start, stop, pause, or resume services, as well as change their startup type (automatic, manual, or disabled) or the user account under which they run. For system administrators, this is pure gold.
The Network tab displays real-time information. which processes are establishing network connectionsThis includes information such as local and remote IP addresses, ports, and connection status. It's very useful for detecting programs communicating with suspicious addresses or identifying which application is saturating your bandwidth.
For example, if you encounter a "browlock" or a website that blocks your browser with constant dialog boxes, you can use the Network tab to locate it. the browser's specific connection to that domain and close it from Process Hacker, without needing to kill the entire browser process and lose all open tabs, or even block suspicious connections from CMD if you prefer to act from the command line.
The Disk tab lists the read and write activities performed by system processes. From here you can detect applications that overload the disk without apparent reason or identify suspicious behavior, such as a program that writes massively and could be encrypting files (typical behavior of some ransomware).
Advanced features: handles, memory dumps, and "hijacked" resources
In addition to basic process and service control, Process Hacker incorporates very useful tools for specific scenariosespecially when deleting locked files, investigating strange processes, or analyzing application behavior.
A very practical option is Find handles or DLLsThis feature is accessible from the main menu. Imagine you try to delete a file and Windows insists that it's "being used by another process" but doesn't tell you which one. With this function, you can type the file name (or part of it) in the Filter bar and click Find.
The program tracks the handles (resource identifiers) and DLLs Open the list and show the results. When you locate the file you're interested in, you can right-click and choose "Go to owning process" to jump to the corresponding process in the Processes tab.
Once that process is highlighted, you can decide whether to end it (Terminate) to release the file and be able to delete locked filesBefore you do this, Process Hacker will display a warning reminding you that you may lose data. Again, it's a powerful tool that can get you out of a bind when all else fails, but it should be used with caution.
Another advanced feature is the creation of memory dumpsFrom a process's context menu, you can choose "Create dump file…" and select the folder where you want to save the .dmp file. These dumps are widely used by analysts to search for text strings, encryption keys, or malware indicators using tools such as hex editors, scripts, or YARA rules.
Process Hacker can also handle .NET processes more comprehensively than some similar tools, which is useful when debugging applications written on that platform or analyzing malware based on .NET.
Finally, when it comes to detecting resource-consuming processesSimply click on the CPU column header to sort the process list by processor usage, or on Private bytes and I/O total rate to identify which processes are hogging memory or overloading I/O. This makes locating bottlenecks very easy.
Compatibility, driver, and security considerations
Historically, Process Hacker operated on Windows XP and later versions, requiring .NET Framework 2.0. Over time the project has evolved, and the most recent versions are geared towards Windows 10 and Windows 11, both 32 and 64 bits, with somewhat more modern requirements (certain builds are known as System Informer, spiritual successor to Process Hacker 2.x).
In 64-bit systems, a delicate issue comes into play: kernel-mode driver signing (Kernel-Mode Code Signing, KMCS). Windows only allows loading drivers signed with valid certificates recognized by Microsoft, as a measure to prevent rootkits and other malicious drivers.
The driver that Process Hacker uses for its more advanced functions may not have a system-accepted signature, or it may be signed with test certificates. This means that, in a standard 64-bit Windows installationThe driver might not load and some "deep" features will be disabled.
Advanced users can resort to options such as activate Windows "test mode" (which allows loading trial drivers) or, in older versions of the system, disabling driver signature verification. However, these maneuvers significantly reduce system security, as they open the door for other malicious drivers to slip through unchecked.
Even without a driver loaded, Process Hacker is still a very powerful monitoring toolYou'll be able to see processes, services, network, disk, statistics, and much other useful information. You'll simply lose some of your ability to terminate shielded processes or access certain very low-level data.
In any case, it's worth remembering that some antivirus programs will detect Process Hacker as Riskware or PUP Precisely because it can interfere with security processes. If you use it legitimately, you can add exclusions to your security solution to prevent false alarms, always being aware of what you're doing.
For anyone who wants to better understand how their Windows behaves, from advanced users to cybersecurity professionals, Having Process Hacker in your toolbox makes a huge difference when it comes time to diagnose, optimize, or investigate complicated problems in the system.
Editor specialized in technology and internet issues with more than ten years of experience in different digital media. I have worked as an editor and content creator for e-commerce, communication, online marketing and advertising companies. I have also written on economics, finance and other sectors websites. My work is also my passion. Now, through my articles in Tecnobits, I try to explore all the news and new opportunities that the world of technology offers us every day to improve our lives.