- Windows and your applications establish numerous legitimate connections, but it is vital to identify anomalous processes and IPs that may indicate malware or untrusted software.
- Tools such as netstat, Resource Monitor, Task Manager, and Process Explorer allow you to link each connection to a specific process and analyze its legitimacy.
- Checking IP reputation on VirusTotal or AbuseIPDB, reviewing paths and digital signatures, and using the firewall to block suspicious programs strengthens security.
- Keeping Windows updated, using antivirus software, avoiding risky downloads, and properly configuring the firewall greatly reduces the likelihood of attacks exploiting vulnerabilities and insecure WiFi networks.

You may have noticed that you Windows connects to suspicious servers that you don't recognize and have wondered if your PC has been hacked. In those cases, it's normal to be alarmed. Between antivirus alerts, firewall warnings, and endless lists of connections, it's normal to feel overwhelmed and not know how to distinguish what's normal from what could be dangerous.
The reality is that Windows constantly communicates with the Internet.You need connections to update, validate licenses, synchronize data, or simply to ensure your programs function correctly. The problem arises when an unknown, misconfigured, or downright malicious application starts connecting to suspicious servers without your knowledge. This article will show you how to identify these connections, how to determine if they are legitimate, and what to do to protect your computer.
Why Windows seems to connect to so many servers (and it's not always a bad thing)
When you first look at your computer's connections, it's quite a shock: dozens of IPs, strange ports, and processes with names you've never heard of. The logical thing to think is, "Something weird is going on here," but A large part of that activity is completely legitimate and harmless to your PC.
Windows and many applications need connect to trusted servers For the most routine tasks: downloading updates, verifying digital signatures, synchronizing files, uploading ads or usage statistics, validating licenses, etc. For example, Windows UpdateYour browser, your email client, or even a simple text editor may be connecting in the background.
It is also normal for the same program to open several simultaneous connections.A browser, for example, establishes different connections for each tab and for each resource (images, scripts, stylesheets, etc.). Therefore, seeing many open connections is not synonymous with infection.
The real problem arises when Windows connects to suspicious servers.Especially if it does so persistently, consumes a lot of resources, or appears in unusual system locations (temporary folders, misspelled locations, uncommon directories, etc.). That's where you need to investigate.

How to view active connections in Windows using netstat and other tools
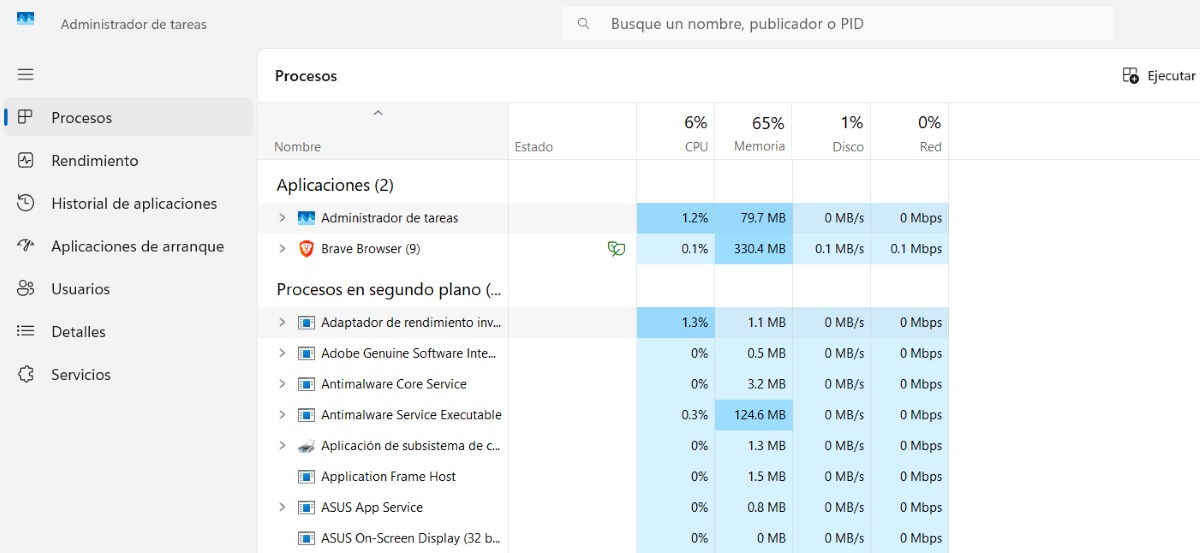
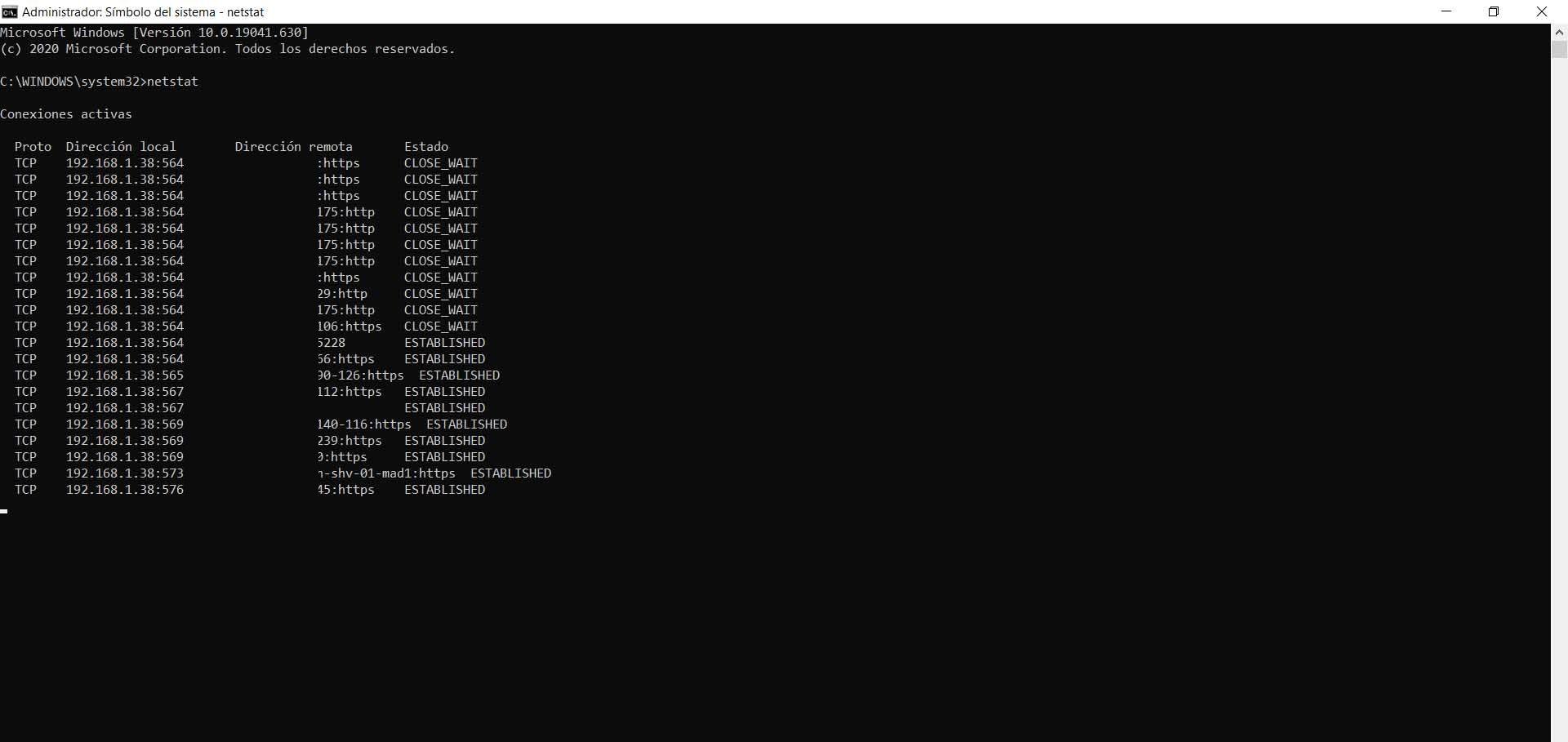
The classic form of Check which connections your PC has open in Windows It's using the console with the command netstatCombining it with other system utilities such as NirSoft tools You can find out exactly which program is behind each connection.
If you run the command in the terminal netstat -ano, you will get a detailed list of active connections, ports used, status and the associated PID (Process Identifier)You'll see both incoming and outgoing connections, and you'll be able to quickly identify which IP addresses are communicating with your computer.
The next step is to link those PIDs to specific programsTo do this you can use tasklist From the console itself, or the Task Manager. This way you'll know if a connection is being made by your browser, a system service, Windows Update, or an unknown application.
In addition to netstat, Windows integrates the Resource Monitorwhere, in the Network tab, you can see which processes are sending and receiving data, which addresses they are connecting to, and how much traffic they are consuming; if you need to delve deeper, you can learn how to Master the Task Manager to better interpret that data.
For an even deeper analysis, Sysinternals Process Explorer (Microsoft's official tool) lets you see which processes have open internet connections, who signed the executable, where it's installed, and what other files or registry keys it uses. A good resource for finding out if Windows is connecting to suspicious servers.
Identify if a connection or IP address is suspicious
Once you've located an IP address or process that you don't recognize, the important thing is to find out if it's really something dangerous or simply a legitimate service you were unaware of. Here are the steps to follow:
- Examine the reputation of the IP addressCopy the IP address that caught your attention and check its status on platforms like VirusTotal or AbuseIPDB. These websites indicate whether that IP address has been associated with botnets, malware servers, phishing attacks, or compromised proxies.
- In parallel, review the process that is using that IP address.Using the PID displayed by netstat or Resource Monitor, open Task Manager, go to the "Details" tab, and locate that identifier. Check the executable's name, its path on the disk, and, if necessary, open "Properties" to view information such as the creation date or digital signature.
If the file is located in an unusual location, it does not have a reliable digital signature. If you find it related to pirated software, cracks, keygens, or downloads from dubious sources, you should be suspicious. If in doubt, you can search for the executable's name on websites like File.net, which catalog many common processes and help determine whether they are system programs or not.
Using Task Manager to hunt for malicious processes in Windows
The Task Manager is probably The most underrated tool for detecting if Windows is connecting to suspicious serversWindows includes it by default and, when used properly, it can get you out of more than one tight spot.
To open it, you can right-click the Start button and choose “Task Manager”, or use the keyboard shortcut Ctrl + Alt + Delete and select it from the menu. Once inside, in the “Processes” tab you will see what is running in real time and what percentage of CPU, memory, disk and network each element is consuming.
When you suspect something is wrong (slowdowns, fan running continuously, slow connection), Look for processes that you don't recognize and that are consuming a lot of resources.Ask yourself: “Do I recognize this application?” and “Does it make sense that it’s using so much CPU or network right now?”
- If you identify a strange process, right-click and go to “Properties”There you'll see the file's full path, the manufacturer, the version, and other information that will help you decide if it's trustworthy. If you still have doubts, you can search for its name online or on specialized websites to check if it's classified as safe or malicious.
- If you confirm that it is a malicious or highly suspicious processYou can select it and click "End task" to stop it from running. If it really was malware, you should notice a performance improvement, but this doesn't mean the problem is completely gone: it's essential to run a full scan with your antivirus software right afterward.
Process control in macOS and alternatives to netstat
If you also have Apple devices, it's useful to know that macOS has an equivalent tool for controlling processes and connections, although the access method is different. The key tool here is called “Activity Monitor”. It's the one that will help us detect if Windows connects to suspicious servers.
When you open Activity Monitor you will see a list of all running apps and processesJust like in Windows, many of the names might not sound familiar, but that doesn't automatically mean they're malicious. You can click on any of them and then click on the information icon (the "i" at the top) to see details such as their disk path or the percentage of memory they're using.
For a more technical analysis of connections in macOSThe terminal is also your ally. Commands like lsof -i They show you which processes are using network ports and which remote addresses they are communicating with, similar to netstat in Windows.
If you detect a suspicious process on your Mac, you can select it in Activity Monitor. and tap the "X" icon to close it. And, if despite everything you don't find anything unusual but the device continues to malfunction, the system itself allows you to run diagnostics from the gear icon located in the application's top bar.
Practical protocol for analyzing suspicious IPs and processes
When the alarm goes off because you see a strange IP address or an unknown processThe worst thing you can do is act blindly. It's much more effective to follow a short, step-by-step protocol that allows you to make informed decisions. Here it is:
- Gather informationNote the suspicious IP address, PID, process name, and the path to the executable file. With this information, check the IP address's reputation on VirusTotal or AbuseIPDB and the process's origin using Process Explorer or the file's properties.
- Block IP address from Windows firewallThere you can create a new outbound rule and choose whether you want to block by program or by port, so that the software can no longer connect to the Internet.
- Perform a full system scan with your antivirus software. (Windows Defender, Malwarebytes, or another trusted solution). Let it scan all drives and pay special attention to files linked to the process you identified as suspicious.
- Document what has happenedInclude the date and time of detection, IP address, PID and process name, VirusTotal or AbuseIPDB results, and the actions you took (blocking, deleting, quarantining, etc.). This small "incident log" is very useful if similar symptoms reappear later.
Malicious processes, malware, and performance: when your PC sluggishes
Does Windows really connect to suspicious servers? Often, the first sign that something is wrong isn't an error message, but rather that the computer starts running slower than usual.
In most cases there is no cause for concernOften, this happens because the system is installing updates, several resource-intensive applications are open simultaneously, or the internet connection is being used by other people in the house. But sometimes, this performance drop can be due to malware running in the background.
However, it is true that Viruses and other types of malicious code can take advantage of your computer To mine cryptocurrencies, send spam, participate in distributed attacks, or steal information. All of this consumes CPU, memory, and bandwidth without you even realizing it.
While having an up-to-date antivirus greatly reduces the risk, no solution is 100% foolproof. Occasionally, a virus might slip through, especially if you install pirated software, open suspicious email attachments, or connect USB devices from unknown sources. That's why it's so important. knowing how to identify anomalous processes and connectionsIt gives you a second layer of defense beyond the antivirus.
Best practices for reducing the risk of dangerous connections
In addition to updating Windows and its drivers, there are a number of habits which drastically reduce the chances of your connections ending up on malicious servers or that someone might take advantage of security flaws.
- Be wary of suspicious emailsGolden rule: Don't open messages from unknown senders or download unexpected attachments, even if they appear to be from a legitimate source. Many attacks begin with a simple phishing email.
- Use strong and different passwords for each serviceAvoid using obvious personal information (dates of birth, phone numbers, family names) and opt for long combinations of letters, numbers and symbols, preferably managed with a password manager.
- Browse trusted websites and avoid downloads from dubious sitesThis is especially true when it comes to free programs, cracks, pirated content, or unofficial installers. That's where most malware disguises itself as a "gift."
- Avoid public or open WiFi networksIn cafes, airports, or shopping malls, it's best to avoid logging into banks, corporate email, or other critical services. If you have no other option, consider using a VPN to encrypt your traffic and make it harder for other users on the same network to spy on or manipulate your connections.
- Regularly review your Windows firewall settings. To ensure it's enabled and working. If, after enabling it, you notice that some legitimate applications (such as browsers, game clients, or messaging apps) stop connecting, you can adjust specific rules instead of disabling the entire firewall, which is a bad idea from a security standpoint.
Understanding what your PC does when it “talks” to the Internet It gives you a valuable sense of control. By understanding your processes, monitoring connections, and applying a few best practices, you can minimize both the risk of Windows connecting to genuinely dangerous servers and unnecessary panic over activities that, while noisy, are perfectly normal.
Editor specialized in technology and internet issues with more than ten years of experience in different digital media. I have worked as an editor and content creator for e-commerce, communication, online marketing and advertising companies. I have also written on economics, finance and other sectors websites. My work is also my passion. Now, through my articles in Tecnobits, I try to explore all the news and new opportunities that the world of technology offers us every day to improve our lives.