- Akira claims to have exfiltrated 23 GB of Apache OpenOffice documents; the list remains without independent verification.
- The Apache Software Foundation is investigating and says it does not possess the type of data described and has not received a ransom demand.
- There is no indication that public downloads or installations of OpenOffice are compromised.
- The group operates with double extortion and has attacked in Europe; reinforced measures are recommended for organizations in the EU and Spain.

El Akira ransomware group ha published on their leaks portal that broke into Apache OpenOffice systems and stole 23 GB of corporate informationAlthough the announcement has generated concern within the community, there is no independent verification that confirms the authenticity of the data or the actual scope of the incident.
Apache OpenOffice It is a free and open source office suite with tools equivalent to Writer, Calc, Impress, Draw, Base, and Math, available for Windows, Linux, and macOS. As of today, There is no indication that download infrastructure or end-user facilities have been affected, since they are separate from the development servers.
Scope of the alleged theft

According to claims attributed to Akira, the loot would include personal records and internal files The group claims to possess sensitive documentation and plans to release it if its demands are not met.
- Physical addresses, telephone numbers, and dates of birth
- Driving licenses and social security numbers
- Credit card data and financial records
- Confidential internal files
- Numerous reports on application problems and development issues
In their message, the attackers emphasize that “23 GB of corporate documents will be uploaded” and describe an intrusion that would have affected the foundation's operating systems. The tactic fits with the doble extorsión: stealing information and pressuring people with its publication in addition to encryption.
State of the research and position of the Apache Software Foundation
For the time being, the Apache Software Foundation (ASF) has not confirmed the commitment of the Apache OpenOffice systems. The organization has indicated that it is investigating the situation and that the Akira listing remains unverified, while various specialized media outlets requested official comments.
In a recent communication, the ASF indicated that has not received any ransom demands And that, given the open-source nature of the project, it does not have the employee dataset described by the attackers. The foundation emphasizes that OpenOffice is developed in public channels and encourages users to download the latest version only from the official website.
Furthermore, the ASF points out that the download infrastructure is separate from the development servers, therefore there is no evidence of compromised public software or direct risk to user facilities at this stage.
Who is Akira and how does he operate?
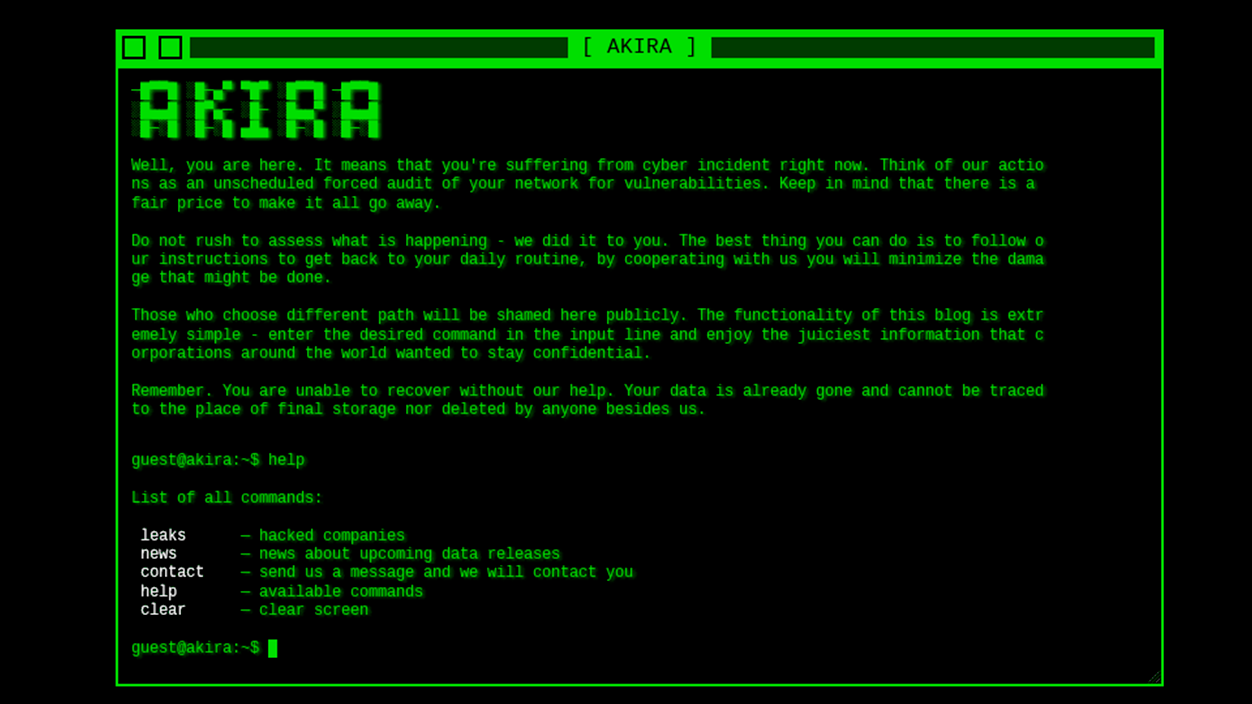
Akira is a ransomware-as-a-service (RaaS) operation active since 2023, with hundreds of intrusions documented in the United States, Europe and other regions, and with a history of collecting millions in ransoms.
The group employs tactics of doble extorsión and develops variants for Windows and Linux/VMware ESXi. A Bitdefender report (March 2025) even noted the use of webcams of victims to gain leverage during negotiations.
In underground forums they communicate in Russian and their malware is usually Avoid computers with Russian keyboard layouts, a pattern observed in other gangs that seek to avoid attacking certain environments.
Implications for Spain and the European Union
If the authenticity of the leaked data is confirmed, they could be activated notification obligations Under the GDPR, personal data must be subject to authorities such as the Spanish Data Protection Agency (AEPD), and in certain sectors, NIS2 requirements apply to essential or digital service providers. The potential misuse of personal data would increase the risk of phishing e ingeniería social against collaborators and suppliers.
For Spanish and European organizations that use OpenOffice (or that coexist with it) Linux/ESXi environments), it is advisable to reinforce the monitoring of anomalous activityIsolate backups, apply MFA, segment networks, and keep patches up to date, reducing the window for exploiting vulnerabilities.
Mitigation measures and good practices

In the absence of official confirmation regarding the scope, it is prudent to exercise extreme caution. safety hygiene and limit the attack surface on endpoints and servers, prioritizing prevention, detection, and response controls.
- Download OpenOffice only from openoffice.org and avoid third-party links on social networks or forums.
- Verify the integrity of installers and always keep the latest version.
- Apply MFA to administrative and VPN accessReview password policies.
- Segregate and encrypt backups (offline/immutable) and test its periodic restoration.
- Hardening ESXi hypervisors and Linux/Windows servers; inventory and continuous patching.
- Implement EDR/antimalware con capacidad de exfiltration and ransomware detection.
- Anti-phishing training and drills incident response.
It is also recommended to activate blocklists and monitoring of similar domains (typosquatting), as well as alerts about possible data publications on leak sites to react quickly.
The situation continues to evolve: Akira maintains the pressure with his announcement, while the ASF investigates and calls into question the plausibility from the allegedly stolen database. As of today, the risk to end users seems limitadoHowever, the incident reinforces the need to download only from official sources and to raise the bar for security in organizations in Spain and the EU.
I am a technology enthusiast who has turned his "geek" interests into a profession. I have spent more than 10 years of my life using cutting-edge technology and tinkering with all kinds of programs out of pure curiosity. Now I have specialized in computer technology and video games. This is because for more than 5 years I have been writing for various websites on technology and video games, creating articles that seek to give you the information you need in a language that is understandable to everyone.
If you have any questions, my knowledge ranges from everything related to the Windows operating system as well as Android for mobile phones. And my commitment is to you, I am always willing to spend a few minutes and help you resolve any questions you may have in this internet world.