- Crimson Collective claimed access to Nintendo systems and released a screenshot with internal folder names.
- Nintendo later denied any breach of its servers and ruled out leaks of personal or development data.
- The group operates through extortion and opportunistic access, exploiting exposed credentials, cloud-based flaws, and web vulnerabilities; Red Hat (570 GB) is a notable example.
- Containment measures, forensic auditing, MFA, and least privilege are recommended for incidents of this type.

The group Crimson Collective claims to have broken into Nintendo systems, in an episode that once again puts the spotlight on the digital protection of large technology companiesAttention is focused on the alleged intrusion and the scrutiny of the released evidence, amid a particularly sensitive context for corporate cybersecurity.
The alert It became popular after a publication on X (formerly Twitter) amplified by Hackmaniac, where a was shown capture of the directory tree (which you can see in the image below) of what appear to be internal Nintendo resources, with references such as “Backups”, “Dev Builds” or “Production Assets”. Nintendo denies this attack and independent verification of that evidence is ongoing and, as usual, the authenticity of the materials is evaluated with caution.
Case timeline and official status
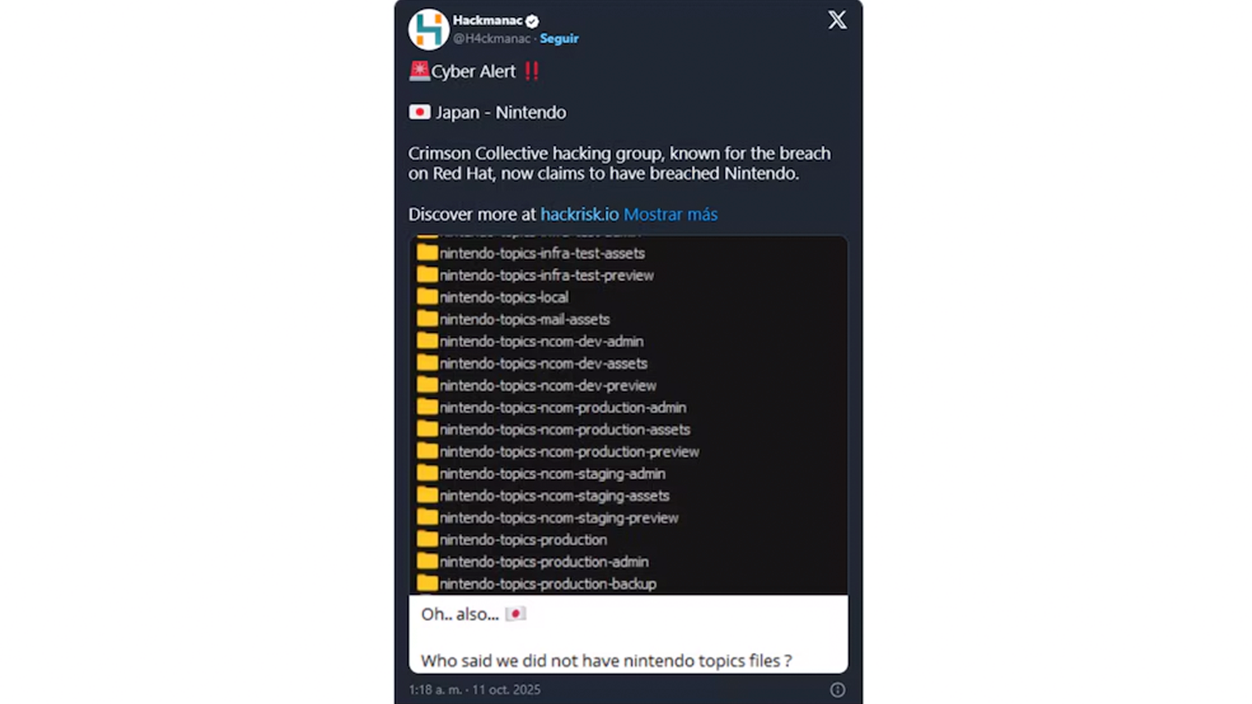
According to the evidence gathered, the claim was first spread on messaging and social media channels, with Crimson Collective sharing partial entrance exams and its extortion narrative. The group, which typically operates through Telegram, often displays lists of folders or screenshots to reinforce the credibility of its ads before negotiating with victims.
In a later update, Nintendo explicitly denied the existence of a breach that compromised personal, business, or development data. In statements to the Japanese media outlet Sankei Shimbun dated October 15, the company stated that there was no evidence of deep access to its systems; at the same time, it was mentioned that some web servers related to your page would have shown incidents, with no confirmed impact on customers or internal environments.
Who is Crimson Collective and how does it usually operate?

Crimson Collective has gained notoriety for targeting its attacks on firms of technology, software and telecommunications. Its most repeated pattern combines target research, breaking into poorly configured environments, and then publishing limited evidence to pressure. Often, the collective exploits exposed credentials, cloud configuration errors and vulnerabilities in web applications, to then announce economic or media demands.
Recent technical research describes a very cloud-linked approach: Attackers are trawling repositories and open sources for keys and tokens leaked using open source tools. aimed at discovering “secrets”.
When they find a viable vector, They try to establish persistence and escalate privileges on cloud platforms (for example, with ephemeral identities and permissions), with the aim to exfiltrate data and monetize accessProviders like AWS recommend short-lived credentials, a policy of least privilege, and continuous permissions review as lines of defense.
Incidents recently attributed to the group

In recent months, attacks attributed to Crimson Collective include high-profile targetsThe case of Red Hat stands out, of which The group claims to have stolen about 570 GB of data from around 28.000 internal repositories.. They have also been linked to Nintendo site defacement At the end of September, there were already intrusions against telecommunications companies in the region.
- Red Hat: massive extraction of internal information from its ecosystem of private projects.
- Telecommunications (e.g., Claro Colombia): campaigns with extortion and selective publication of evidence.
- Nintendo Page: unauthorized modification of the site at the end of September, attributed to the same group.
Implications and potential risks
If such an intrusion were to be confirmed, access to backups and development materials could expose critical assets in the production chain: internal documentation, tools, content being created, or infrastructure information. This opens doors to reverse engineering, exploitation of vulnerabilities and, in extreme cases, to piracy or undue competitive advantage.
In addition, access to internal keys, tokens or credentials would facilitate lateral movements to other environments or providers, with a possible domino effect in the supply chainAt the reputational and regulatory level, the impact would depend on the actual scope of the exposure and the nature of the data that may be compromised.
Expected response and good practices in the industry

In the face of such incidents, The priority is to contain and eradicate unauthorized access, activate a forensic investigation and strengthen identity and access controls.It's also key to review cloud configurations, eliminate attack vectors, and apply telemetry to detect anomalous activity that may indicate attacker persistence.
- Immediate containment: Isolate affected systems, disable exposed credentials, and block exfiltration routes.
- Forensic audit: reconstruct the timeline, identify vectors and consolidate evidence for technical teams and authorities.
- Access hardening: key rotation, mandatory MFA, least privilege, and network segmentation.
- Regulatory transparency: Notify agencies and users when appropriate, with clear guidelines to enhance individual security.
With the Nintendo's denial about the alleged gap, The focus shifts to the technical verification of the evidence presented by Crimson CollectiveHey, the reinforcement of controls to avoid further scares. In the absence of conclusive evidence, The prudent course of action is to maintain vigilance, strengthen cloud configurations, and strengthen collaboration with response teams and vendors., as the group has already demonstrated the ability to exploit exposed credentials and configuration errors on a large scale.
I am a technology enthusiast who has turned his "geek" interests into a profession. I have spent more than 10 years of my life using cutting-edge technology and tinkering with all kinds of programs out of pure curiosity. Now I have specialized in computer technology and video games. This is because for more than 5 years I have been writing for various websites on technology and video games, creating articles that seek to give you the information you need in a language that is understandable to everyone.
If you have any questions, my knowledge ranges from everything related to the Windows operating system as well as Android for mobile phones. And my commitment is to you, I am always willing to spend a few minutes and help you resolve any questions you may have in this internet world.
